The tombstone lifetime in an Active Directory forest determines how long a deleted object - aka a ‘tombstone’ - is retained in Active Directory. The tombstone lifetime is determined by the value of the tombstoneLifetime attribute on the Directory Service object in the configuration directory partition.
Tombstone Lifetime assists in removing objects from replicated servers and preventing restores from reintroducing a deleted object. Actually when an object is deleted from Active Directory, it is not physically removed from the Active Directory for some days. Instead, the Active Directory sets the‘isDeleted’ attribute of the deleted object to TRUE and move it to a special container called ‘Tombstone’.
- Windows 2000 (all SPs) = 60 days
- Windows Server 2003 without SP = 60 days
- Windows Server 2003 with SP1 = 180 days
- Windows Server 2003 R2 with SP1 installed with both R2 discs = 60 days
- Windows Server 2003 R2 with SP1 installed only with the first R2 Disc = 180 days
- Windows Server 2003 with SP2 = 180 days
- Windows Server 2003 R2 with SP2 = 180 days
- Windows Server 2008 onwards 180 days
The tombstone lifetime attribute remains same on all the domain controllers and it is deleted from all the servers at the same time. This is because the expiration of a tombstone lifetime is based on the time when an object was deleted logically from the Active Directory, rather than the time when it is received as a tombstone on a server through replication.
Reconfiguring Tombstone Lifetime:
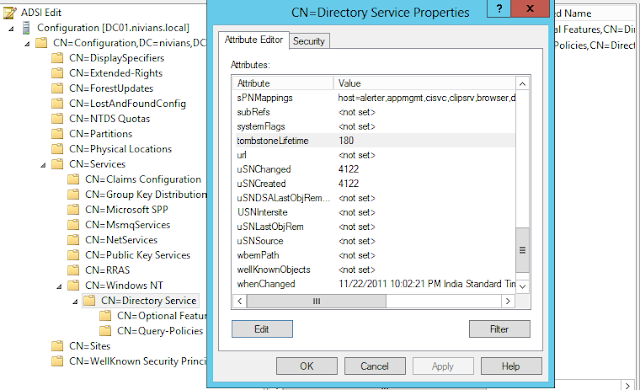
Default period of Tombstone Life time is 180 days in Windows Server 2003 SP2 or later. The default Tombstone Lifetime can be modified through ADSIEDIT console, if necessary.
This attribute is located in the below path:
cn=Directory Service,cn=Windows NT,cn=Services,cn=Configuration,dc=
To Change the Value, Run > ADSIEDIT.msc
Expand: Configuration > CN= Configuration > CN=Services > CN=Windows NT > and right click on CN= Directory Service
You will get an attribute window, Drill down to tombstoneLiftime, and double click it. You will get a field to type down the value, type the value you intended and click OK.
The below picture will help you out to reach the correct object.